Services
Social Engineering
Security does not stop in the cloud, ensure your staff and physical security can handle a malicious actor onsite. Our consultants have a wealth of knowledge in carrying out onsite social engineering. We can tailor-make scenarios to best suit your business objectives.
Assessment Modules
Services
A Physical Social Engineering Engagement involving internal infrastructure and device plantation tests your organisation`s physical security by attempting to infiltrate facilities and plant unauthorised devices on the network. This process aims to uncover weaknesses in physical access controls and employee vigilance, providing a detailed report with findings and recommendations to enhance physical security and prevent unauthorised device installation.
A Physical Social Engineering Engagement without network access tests your organisation`s physical security and employee awareness by attempting to gain unauthorised entry and exploit physical security weaknesses. This process includes activities like tailgating, badge cloning, and manipulating staff, providing a detailed report with findings and recommendations to strengthen physical security and improve staff training against social engineering attacks.
A Physical Social Engineering Engagement with network access and badge cloning, tests your organisation`s defences by attempting to physically infiltrate premises and access the network devices. This process includes exploiting physical security vulnerabilities and employee behaviour to plant rogue devices and clone badges, providing a detailed report with findings and recommendations to enhance both physical and network security, and improve staff training against such sophisticated attacks.
We can tailor make an assessment that meets your priorities and requirements.
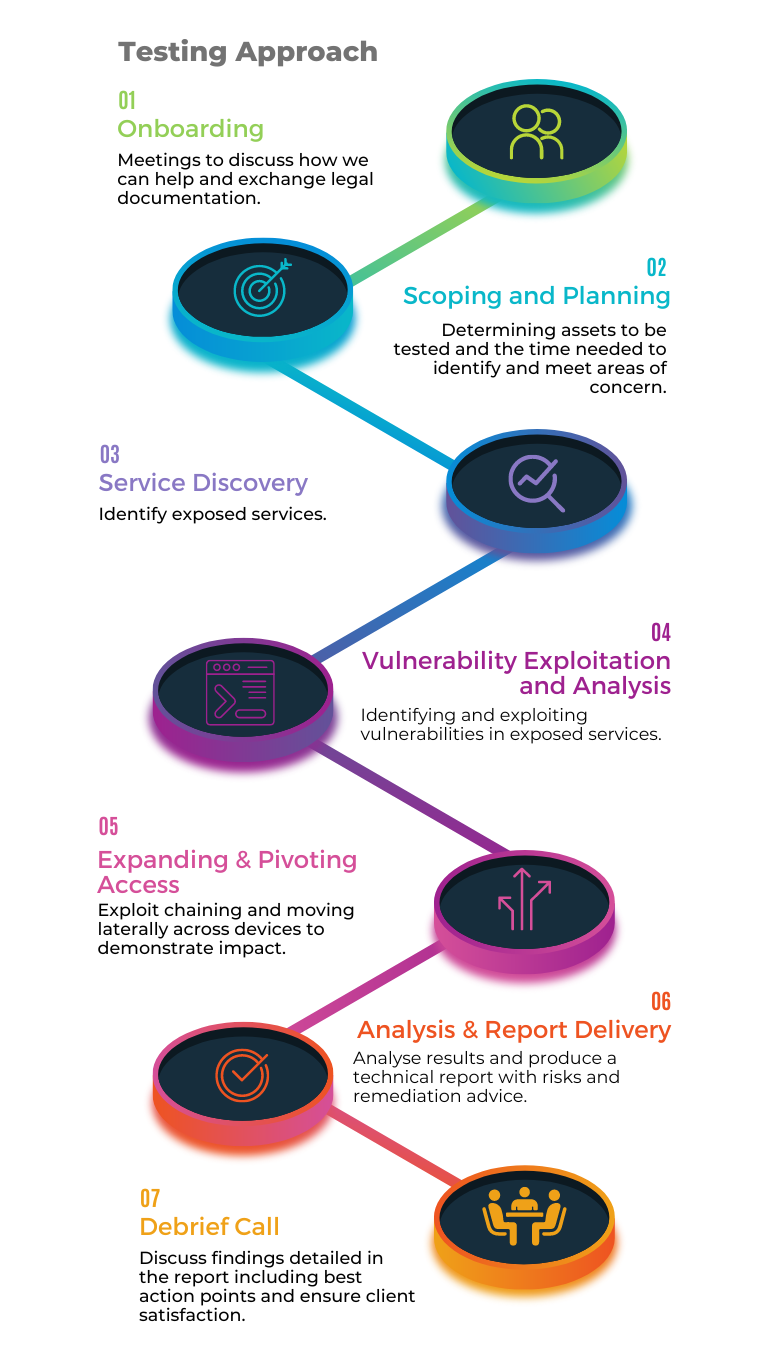
Our Approach
Insight
Gather an understanding of your physical security posture in the eyes of an adversary. Often physical access leads to total compromise of a system. Preventing physical access to both systems and networks adds another layer of defence to your organisation.
Vectors
Assess the foundations of your business and identify attack avenues onsite. Social Engineering typically involves manipulating staff members, our scenarios mimic an adversary in the real world. This could allow sensitive information or access to be obtained.
Assurance
Our consultants hold industry recognised certifications such as CREST and regularly conduct research into the latest threats.
Get a Free Quote Today
Please fill out the form as accurately as possible and we can work on a quote.
 Wolf Network Security
Wolf Network Security