Services
Internal Infrastructure
Using tried and tested methodologies our consultants will identify security concerns on your internal network. At the core of your IT infrastructure, it’s paramount to identify the security risks to ensure you stay secure from potential threats. Our services can include; Internal Penetration Testing, Infrastructure scans, Build reviews and Wireless testing.

Assessment Modules
Services
An Internal Infrastructure Penetration Test involves simulating an insider attack to evaluate the security of your internal network and systems. This assessment identifies vulnerabilities such as misconfigurations, weak passwords, and access control issues, including attack chaining and pivoting to attempt to compromise the domain. Providing a detailed report with findings and recommendations to strengthen your internal defences against potential internal threats.
Workstation and Server Build Reviews involve assessing the security configurations of your workstations and servers against industry benchmarks and best practices. This assessment identifies misconfigurations, vulnerabilities, and compliance gaps. Providing a detailed report with findings and recommendations to ensure your systems are securely configured and aligned with industry best practices.
Content security reviews allow you to test Data Loss Prevention (DLP) technical controls and content moderation are working as expected.
A Wireless Security Assessment involves evaluating the security of your wireless networks to identify vulnerabilities and potential entry points for attackers. This assessment includes testing for weak encryption, unauthorised access points, and misconfigurations. Providing a detailed report with findings and recommendations to strengthen your wireless network security.
An Active Directory Security Review involves thoroughly assessing your Active Directory environment to identify security weaknesses and misconfigurations. This assessment includes Password analysis, evaluating user permissions, group policies, authentication methods, and other critical settings. Providing a detailed report with findings and recommendations to enhance the security and integrity of your Active Directory infrastructure.
Desktop Breakouts involve assessing the security configurations and gain an insight into how a malicious user could abuse the system to attempt to escape the controlled environment or escalate privileges.
A Mobile MDM (Mobile Device Management) Review involves evaluating the security and management of mobile devices within your organisation, guided by NCSC (National Cyber Security Centre) guidelines. This assessment checks compliance with best practices for device configuration, data protection, application management, and access controls.
A Credentialed or Authenticated Scan involves using valid login credentials to perform a thorough scan of systems from the perspective of an authenticated user. This type of scan provides deeper visibility into the internal environment, allowing the tester to identify vulnerabilities such as missing patches, misconfigurations, or weak security settings that may not be visible from an external or unauthenticated scan.
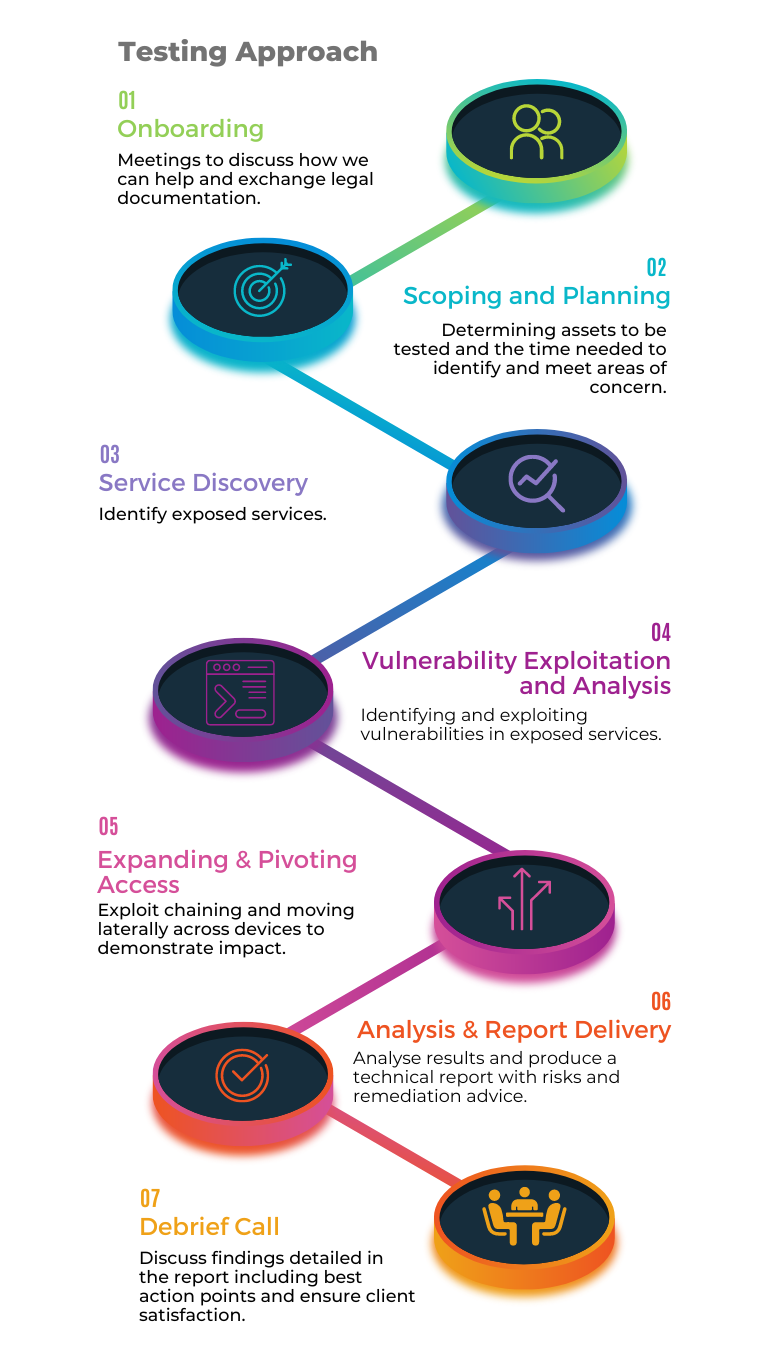
Our Approach
Find Vulnerabilities
Gather an understanding of your internal security posture. If a device was to become compromised on the internal domain, what exploitable services could they use to obtain domain compromise? We can provide a comprehensive assessment which covers low-hanging fruit and manual findings.
Communication
We understand communication is key to a good Penetration test. We will schedule a kick-off call to discuss any areas of concern to the business and take the time to understand fragile devices. Critical findings will be communicated during the assessment followed by a wash-up call to discuss findings.
Additional Services
Wireless Security Assessment, Server & Workstation Build reviews, Mobile MDM and Content Security Reviews can be added for in-depth coverage of your internal infrastructure.
Assurance
Our consultants hold industry recognised certifications such as CREST and regularly conduct research into the latest threats.
Get a Free Quote Today
Please fill out the form as accurately as possible and we can work on a quote.
 Wolf Network Security
Wolf Network Security